Just a basic blog—snagging random stuff that catches our eye—nothing else, really...
Monday, December 31, 2018
Home - UK Cohousing Network
The Monthly – Feature 12-05
INFO 4601/5601 Readings (Spring 2018) - Google Docs
Cyber criminals outspend businesses in cyber security battle
Sunday, December 30, 2018
Saturday, December 29, 2018
Vision Problems : National Multiple Sclerosis Society
Study Finds Diversity Boosts Innovation in U.S. Companies
About verified accounts
Friday, December 28, 2018
Home · obsproject/obs-studio Wiki · GitHub
Thursday, December 27, 2018
Spouse Immigration-UK : British Expat Wiki
The Most Surprising Symptoms of Multiple Sclerosis | Everyday Health
https://www.everydayhealth.com/multiple-sclerosis/symptoms/the-most-surprising-symptoms-of-multiple-sclerosis/
The Uluru Statement from the Heart by Galarrwuy Yunupingu | Daily Review: Film, stage and music reviews, interviews and more.
https://dailyreview.com.au/book-extract-12/63704/
Wednesday, December 26, 2018
Senate Report No. 93-1183
Why privacy regulations are no longer a pipe dream - Axios
https://www.axios.com/privacy-regulations-no-longer-pipe-dream-3b1691eb-9614-400e-84c1-67095a61b385.html
Legislative History of the Privacy Act of 1974: Military Legal Resources (Federal Research Division: Customized Research and Analytical Services, Library of Congress)
http://www.loc.gov/rr/frd/Military_Law/LH_privacy_act-1974.html
Monday, December 24, 2018
Blogspot, BlogTHIS! - Blogger Publish | Ask MetaFilter
"American Nightmare" Is an Antidote to Misguided Faith in Liberal Politics
https://truthout.org/articles/american-nightmare-is-an-antidote-to-misguided-faith-in-liberal-politics/
Howard Roark's Courtroom Speech - Work the System
https://www.workthesystem.com/getting-it/howard-roarks-courtroom-speech/
Wrekin (The Marches Line) – demo – Wheal Alice Music
Sunday, December 23, 2018
Saturday, December 22, 2018
Mac Or MacBook Doesn’t Recognize External Drives, Troubleshooting Tips - AppleToolBox
‘Transgender’ Could Be Defined Out of Existence Under Trump Administration
Steel Slat
http://twitter.com/realDonaldTrump/status/1076239448461987841
Friday, December 21, 2018
Quickly Determine the Theme File WordPress is Loading on a Page — WPShout
How To Enable HTTPS On Your Blogger Blog With Custom Domain
Humans harass and attack self-driving Waymo cars
Thursday, December 20, 2018
Our Team | APB Speakers
Honoring CompTIA’s 2017 Tech Champions at Fly-In
Wednesday, December 19, 2018
Tuesday, December 18, 2018
Presidential Speeches | Miller Center
Presidential Speeches | Miller Center
Here: https://t.co/5XbSvEPviN
Monday, December 17, 2018
“The Great AI Paradox”
Interactive Statistics -- One-way ANOVA from Summary Data
Intelligent isn’t immune, smart isn’t safe: IoT and associated threats | ITProPortal
https://www.itproportal.com/features/intelligent-isnt-immune-smart-isnt-safe-iot-and-associated-threats/
Sunday, December 16, 2018
Saturday, December 15, 2018
Brackets - A modern, open source code editor that understands web design.
Friday, December 14, 2018
Wednesday, December 12, 2018
Statement regarding hoax article | NORMA: International Journal for Masculinity Studies
Developments in the field of information and telecommunications in the context of international security – UNODA
Since that time there have been annual reports by the Secretary-General to the General Assembly with the views of UN Member States on the issue:
Freight Rate Calculator: Freight Shipping Costs via Air, Ocean, Sea | Freightos
Tuesday, December 11, 2018
How To Enable HTTPS On Your Blogger Blog With Custom Domain
How to Point a Domain to Blogger
The Only Guide You Need To Setup BlogSpot Custom Domain
How To Set Up a Custom Domain in Blogger - The Right Way! - Wonder Forest
Tax Advice For US Expats Living In The UK - Experts for Expats
UK/US Dual Citizens Tax Guidance - Experts for Expats
Monday, December 10, 2018
Is It “Techno-Chauvinist” & “Anti-Humanist” to Believe in the Transformative Potential of Technology?
Crime Data Downloads
OCR Fines Florida Physicians Group $500,000 for HIPAA Failures
Friday, December 7, 2018
Philanthropy Needs To Take A Hard Look At Its Colonial Roots
Thursday, December 6, 2018
What Our Tech Ethics Crisis Says About the State of Computer Science Education
https://howwegettonext.com/what-our-tech-ethics-crisis-says-about-the-state-of-computer-science-education-a6a5544e1da6
Wednesday, December 5, 2018
Gartner Says By 2020, 60 Percent of Digital Businesses Will Suffer Major Service Failures Due to the Inability of IT Security Teams to Manage Digital Risk
By 2020, 60 percent of digital businesses will suffer major service interruptions | CIO
Tuesday, December 4, 2018
AI winter – update – Piekniewski's blog
Saturday, December 1, 2018
Welcome - Cloud Security Expo London 2019 - Master Your Survival Skills
Thursday, November 29, 2018
Home Routers Under Attack by NSA-Spawned Malware: What to Do
https://www.tomsguide.com/us/routers-malware-upnproxy-eternalsilence,news-28727.html
ElasticSearch server exposed the personal data of over 57 million US citizens
Wednesday, November 28, 2018
New industrial espionage campaign leverages AutoCAD-based malware | ZDNet
https://www.zdnet.com/article/new-industrial-espionage-campaign-leverages-autocad-based-malware/
Emotion shapes the diffusion of moralized content in social networks | PNAS
Nail Your Next Talk or Presentation By Using These 5 Strategies | Inc.com
https://www.inc.com/carol-sankar/nail-your-next-talk-or-presentation-by-using-these-5-strategies.html
Monday, November 26, 2018
Trump Administration’s Strategy on Climate: Try to Bury Its Own Report
Sunday, November 25, 2018
EasyExpat.com - Information for Expatriates, Expat Guides
International Air Freight & Air Shipping Charges, Rates, & Cost | Freightos
Broadband in Coventry - maybe
Saturday, November 24, 2018
FreeRTOS TCP/IP Stack Vulnerabilities Put A Wide Range of Devices at Risk of Compromise: From Smart Homes to Critical Infrastructure Systems | Zimperium Mobile Security Blog
Echo Barrier | Outdoor Sound Barrier | Acoustic Barrier Fence
Versipanel Portable Acoustical Wall for Offices and Studios
Is caller ID spoofing driving you nuts?� - The FCPA Blog - The FCPA Blog
How to Create a Successful Patron Campaign for Your Podcast | Podbean Podcast Blog
Friday, November 23, 2018
How Patreon became a major source of revenue for podcasters
“Is Satoshi Nakamoto Turning in his Virtual Grave?”
“A beginners guide to keeping your crypto safe”
Thursday, November 22, 2018
Monday, November 19, 2018
International Programs - Totalization Agreement with the United Kingdom
International Programs - Totalization Agreement with the United Kingdom
CERTIFICATE OF COVERAGE REQUEST FORM - Select the Request Form Type
International Programs- International Programs and Resources
Medicare coverage when living abroad - Medicare Interactive
Chondrodermatitis nodularis helicis: Symptoms and treatment
Relapsing polychondritis | Genetic and Rare Diseases Information Center (GARD) – an NCATS Program
Friday, November 16, 2018
Thursday, November 15, 2018
The Importance of Existential Intelligence – Awecademy – Medium
Playa Blanca, Tijuana, Baja California — Point2 Homes
The Park At Malibu, Tijuana, Baja California — Point2 Homes
Wednesday, November 14, 2018
Tuesday, November 13, 2018
US joins Russia, North Korea in refusing to sign cybersecurity pact
https://shareblue.com/paris-cybersecurity-pact-united-states-russia-refuse/
The Apollo Breach Included Billions of Data Points | WIRED
Monday, November 12, 2018
On Puritanism - The Faithless Feminist
Meeting Kosovo's clickbait merchants - BBC News
Sunday, November 11, 2018
Mexico Immigration Guide visas, work, Temporary Resident, Permanent Resident, FM2, FM3, Mexican Citizenship
Special Eurobarometer 464a: Europeans’ attitudes towards cyber security - Datasets
PublicOpinion - European Commission 464A
Saturday, November 10, 2018
Trade in with Apple GiveBack - Apple
Friday, November 9, 2018
Traditional Elegance (736119 downloads) - Chronological Resume
750 Cover Letter Templates | MyPerfectCoverLetter
Ancient genomics is recasting the story of the Americas’ first residents
https://www.nature.com/articles/d41586-018-07374-1
Thursday, November 8, 2018
Tweet from Symantec (@symantec)
Our 3,800 cyber security researchers and engineers work to keep us all one step ahead of the bad actors.
(https://twitter.com/symantec/status/1060322407204954114?s=03)
Get the official Twitter app at https://twitter.com/download?s=13
Wednesday, November 7, 2018
283 Cover Letter Templates For Any Job
Choosing the Right Mapping Drone for Your Business Part II: Aerial Imaging and Cameras
Tuesday, November 6, 2018
Monday, November 5, 2018
Perception and action de-coupling in congenital amusia: sensitivity to task demands. - Goldsmiths Research Online
Reduced sensitivity to emotional prosody in congenital amusia rekindles the musical protolanguage hypothesis | PNAS
Cambridge Analytica, the Artificial Enemy and Trump's 'Big Lie'
Information Commissioners Office and the Chair of the Digital, Culture, Media and Sport
Committee's Fake News Inquiry Damian Collins MP to submit information and research
relating to campaigns by SCL, Cambridge Analytica and other actors."
https://www.parliament.uk/documents/commons-committees/culture-media-and-sport/Dr%20Emma%20Briant%20Explanatory%20Essays.pdf
Academic research into the EU Referendum campaign and propaganda during conflicts.
University of Essex, as part of academic research into the EU Referendum campaign and
propaganda during conflicts.
https://www.parliament.uk/documents/commons-committees/culture-media-and-sport/Dr%20Emma%20Briant%20Audio%20File%20Transcripts%20with%20links.pdf
Sunday, November 4, 2018
Are Women More Ethical Than Men? | GGM
Cyber attackers switching to covert tactics
Saturday, November 3, 2018
Tuesday, October 30, 2018
Cimetrics BACnet Explorer
Amazon Patched Multiple IoT Vulnerabilities Affecting Its Smart Devices
Monday, October 29, 2018
Heatmiser and BMW – Better Connected with IFTTT | Heatmiser
No One Can Get Cybersecurity Disclosure Just Right | WIRED
Sunday, October 28, 2018
The White House is wooing tech workers to do tours of duty in government - The Washington Post
132 Women In Cybersecurity To Follow On Twitter
‘War for Talent’ Emerges Amid Skilled Workforce Shortage – WWD
Saturday, October 27, 2018
Amazon fixes security flaws allowing smart home hijacks
https://www.engadget.com/2018/10/21/amazon-fixes-13-iot-security-flaws/
New state-backed espionage campaign targets military and government
https://www.zdnet.com/article/new-state-backed-espionage-campaign-targets-military-and-government-using-freely-available-hacking/
Friday, October 26, 2018
Cybersecurity Needs Women: Here's Why
https://www.forbes.com/sites/laurencebradford/2018/10/18/cybersecurity-needs-women-heres-why/
TRITON Attribution: Russian Government-Owned Lab Most Likely Built Custom Intrusion Tools for TRITON Attackers � TRITON Attribution: Russian Government-Owned Lab Most Likely Built Custom Intrusion Tools for TRITON Attackers | FireEye Inc
ICS Cyber Security | Protect Against Threats - Nozomi Networks
Thursday, October 25, 2018
The U.S. labor shortage is reaching a critical point
Top Five Sectors Exposed to Labor Shortages in 2018 – Industry Insider
Full text of Apple CEO Tim Cook's keynote in Brussels
The pilot shortage isn't changing course. Here's how UPS plans to land new talent.
https://www.courier-journal.com/story/money/companies/2018/09/17/ups-pilot-shortage-new-training-program/1210341002
Airlines are desperate for pilots and it's causing route cancellations - Business Insider
https://www.businessinsider.com/airlines-pilot-shortage-cancelled-routes-2018-8
Wednesday, October 24, 2018
Security Manager - (Pacific Northwest) - Job ID: 666060 | Amazon.jobs
Skills gap stalls construction industry growth, report says | HR Dive
Aerospace Skills Gap: Workforce Declines, As Talent Needs Increase - Area Development
http://www.areadevelopment.com/Aerospace/q3-2015-auto-aero-site-guide/Aerospace-Skills-Gap-Workforce-Declines-Needs-Increase-45711.shtml
One Company’s Solution To The Widening Skills Gap
https://chiefexecutive.net/one-companys-solution-widening-skills-gap/
Monday, October 22, 2018
Study Finds Diversity Boosts Innovation in U.S. Companies | NC State News | NC State University
https://news.ncsu.edu/2018/01/diversity-boosts-innovation-2018/
Sunday, October 21, 2018
Is It “Techno-Chauvinist” & “Anti-Humanist” to Believe in the Transformative Potential of Technology?
Friday, October 19, 2018
Thursday, October 18, 2018
GDPR matchup: The California Consumer Privacy Act 2018
Data breach response plans are no longer optional for public practices. Here’s what yours needs. | INTHEBLACK
Tuesday, October 16, 2018
New Climate Debate: How to Adapt to the End of the World - Bloomberg
Jeff Bezos: Tech will figure out the solutions to abuse
Stephen Hawking warned of 'superhumans' and the end of humanity
Sunday, October 14, 2018
One-Third of US Adults Hit with Identity Theft
Saturday, October 13, 2018
What is the difference between categorical, ordinal and interval variables?
Everything You Need to Know about NERC CIP Compliance by Dave Millier, CRISC - security management, risk, risk management & compliance
Welcome to Triumph Music | Production Music Library
Features - Statistical Test Selector | Laerd Statistics
Cloud Baby Monitor - Unlimited Range Video Baby Monitor
LIRR to Jamaica and Airtrain: Best Way to Get to JFK
Thursday, October 11, 2018
Pearson Correlation - SPSS Tutorials - LibGuides at Kent State University
'The magnitude, or strength, of the association is approximately moderate (.3 < | r | < .5)."
Weight and height have a statistically significant linear relationship (p < .001).
The direction of the relationship is positive (i.e., height and weight are positively correlated), meaning that these variables tend to increase together (i.e., greater height is associated with greater weight).
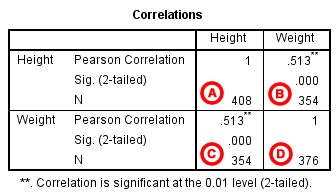
What is the difference between categorical, ordinal and interval variables?
Gender bias in health care may be harming women's health
Wednesday, October 10, 2018
Email and Internet Voting: The Overlooked Threat to Election Security - Common Cause
U.S. GAO - Weapon Systems Cybersecurity: DOD Just Beginning to Grapple with Scale of Vulnerabilities
Monday, October 8, 2018
Tuesday, October 2, 2018
Facebook pulls its Onavo Protect VPN app from Apple's App Store
Friday, September 28, 2018
Tuesday, September 25, 2018
The Hercules System/370, ESA/390, and z/Architecture Emulator
pspp4windows download | SourceForge.net
Monday, September 24, 2018
Cave Junction Man Arrested after Threats to YouTube Employees and CEO - Wild Coast Compass
Friday, September 21, 2018
Could your perception of self-employment be all wrong? | World Economic Forum
http://www.cam.ac.uk/research/news/the-boss-of-me-myths-and-truths-of-self-employment
Thursday, September 20, 2018
The ExecRanks | Schedule a Call to Learn More
Wednesday, September 19, 2018
Click your heels, um, mouse thrice and you've quickly got Ubuntu on Hyper-V in Win 10 Pro • The Register
https://www.theregister.co.uk/2018/09/19/ubuntu_microsoft_hyper_v/
Ryuk Ransomware Emerges in Highly Targeted, Highly Lucrative Campaign | The first stop for security news | Threatpost
Tuesday, September 18, 2018
Cyber criminals outspend businesses in cyber security battle
Businesses collect more data than they can handle, only half know where sensitive data is stored - Help Net Security
Healthcare Data Presents Lucrative Target for Cyberattackers
Continental Automated Buildings Association
(26) IoT and smart buildings and cities (Part 2, the downside) | LinkedIn
Installing and Running Elasticsearch | Elasticsearch: The Definitive Guide [2.x] | Elastic
Research reveals four distinct personality clusters
https://www.medicalnewstoday.com/articles/323092.php
Monday, September 17, 2018
Social Security calculators aim to take the complexity out of deciding when to claim
https://www.cnbc.com/2018/06/27/social-security-calculators-aim-to-take-the-complexity-out-of-deciding.html
Friday, September 14, 2018
The Encyclopedia of Twentieth-Century Fiction - Google Books
https://books.google.com/books/about/The_Encyclopedia_of_Twentieth_Century_Fi.html?id=am1PhEWMqdIC
Vote Is In: Rock Is Night's Big Winner
Wednesday, September 12, 2018
Nearly 600 Russia-Linked Accounts Tweeted About the Health Law - WSJ
https://news.google.com/articles/CAIiEKps7MkWtrLP3dU8nYIIZMAqGAgEKg8IACoHCAow1tzJATDnyxUwiK20AQ
Tuesday, September 11, 2018
Monday, September 10, 2018
Sunday, September 9, 2018
Saturday, September 8, 2018
FAQ | HECM PA
Photography and sharing images guidance
Thursday, September 6, 2018
Fighting ransomware with network segmentation as a path to resiliency - Help Net Security
Defeat Ransomware Attacks with Network Segmentation | BlackRidge
Wednesday, September 5, 2018
CyberEdge 2018 Cyberthreat Defense Report | CyberEdge Group
Scammers pose as CNN's Wolf Blitzer, target security professionals | CSO Online
Tuesday, September 4, 2018
Monday, September 3, 2018
How NotPetya ransomware used legitimate tools to move laterally
Saturday, September 1, 2018
Litigating the Implied Covenant of Good Faith
Exceptions to At-Will Employment in California
Friday, August 31, 2018
Securing Remote Desktop (RDP) for System Administrators | Information Security and Policy
Ex-hacker launches blockchain powered cyber security solution
https://www.information-age.com/ex-hacker-launches-blockchain-powered-cyber-security-solution-123474254/
Thursday, August 30, 2018
Vladimir Putin and Donald Trump's great success in exploiting the rise of nationalist Christianity
https://theconversation.com/amp/vladimir-putin-and-donald-trumps-great-success-in-exploiting-the-rise-of-nationalist-christianity-92963
Blog This! for Google Sites - Google Product Forums
Diplomacy in Cyberspace
Wednesday, August 29, 2018
Don’t hide the menopause – celebrate its creative power | Marina Benjamin | Opinion | The Guardian
https://trib.al/oecWnjH
Tuesday, August 28, 2018
When multi-factor will not save you by Michalis Kamprianis
Monday, August 27, 2018
Tuning in to Musical Students’ Needs | Local | idahostatejournal.com
Cryptojacking Displaces Ransomware As Most Popular Cyberthreat
The memoir by Steve Jobs' daughter makes clear he was a truly rotten person whose bad behavior was repeatedly enabled by those around him (AAPL)
https://finance.yahoo.com/news/memoir-steve-jobs-apos-daughter-133000491.html
Friday, August 24, 2018
Potentially Hazardous Asteroid
https://www.cbsnews.com/news/bennu-asteroid-nasa-osiris-rex-spacecraft-captures-first-images/
Alphabet Chronicle to tackle cybersecurity industry
https://www.cnbc.com/2018/08/23/alphabet-chronicle-cybersecurity.html
Wednesday, August 22, 2018
Feminists Expect More of Men
5 Places That Are Still On Fire | Mental Floss
The World's Oldest Underground Fire Has Been Burning For 6,000 Years
Tweet from Lawrence O'Donnell (@Lawrence)
Every reporter must now ask @LindseyGrahamSC if he still believes in the standard he set for removing a president in the impeachment of Bill Clinton https://t.co/kbF7guFjm7
(https://twitter.com/Lawrence/status/1032105596810612736?s=03)
Monday, August 20, 2018
Digital shadows: dark market report
Amazon’s facial recognition matched 28 members of Congress to criminal mugshots - The Verge
Predatory journals aren't just a scam: they're also how quacks and corporate shills sciencewash their bullshit / Boing Boing
Bogus journals being used to publish fake science – Naked Security
Saturday, August 18, 2018
Wednesday, August 15, 2018
Sex Workers' Rights in the Digital Dystopia - Interview with Ms. Maggie Mayhem — Dead Dialect
Protecting Our Customers through the Lifecycle of Security Threats | Intel Newsroom
Tuesday, August 14, 2018
Tests | Music, Sound and Performance Lab
The 16 best free GarageBand plugins | TechRadar
Video: Fake Science (English subtitles) - Reportage & Documentation
Most Common Cryptocurrency Scam Methods All Investors & Traders Should Know
Monday, August 13, 2018
The unsung story of amusia – The Brain Bank North West
Tone Deafness: A Broken Brain? - The Atlantic
Defending Science - Dr Nick - The Incrementalist
The Genetics of Congenital Amusia (Tone Deafness): A Family-Aggregation Study
Wednesday, August 8, 2018
Endpoint security suites must have these features | CSO Online
Fighting ransomware with network segmentation as a path to resiliency - Help Net Security
Tuesday, August 7, 2018
Most Common Cryptocurrency Scam Methods All Investors & Traders Should Know
Monday, August 6, 2018
Most Common Cryptocurrency Scam Methods All Investors & Traders Should Know
Sunday, August 5, 2018
Top 5 - Most Affordable - Portland Suburbs : Real Estate Agent PDX
iPhone supplier TSMC shut down factories after virus attack - The Verge
https://www.theverge.com/2018/8/4/17651448/iphone-supplier-taiwan-semiconductor-manufacturing-co-tsmc-virus-shut-down
Wednesday, August 1, 2018
OP0182 Gout and dementia in the elderly: a medicare claims study | Annals of the Rheumatic Diseases
Tuesday, July 31, 2018
SMB Cyber Attacks | Hackers Now Prefer Targeting SMBs vs. Enterprise Companies | Pivot Point Security
Information Security Practices Missing in Many Small Businesses:
1. Data backups
2. Security awareness training
3. Patch and configuration management
4. Incident response planning
The Biggest Threat to SMBs are Cyber Attacks - Jive Resource Center
Your SMB Is At Risk: 10 Cyber-security Trends to Watch Out For In 2018 - Netcetera
AbbVie, Pfizer drive 2017 pharma TV ad spending above 2016's tally | FiercePharma
1. AbbVie's Humira: $341 million
2. Pfizer's Lyrica: $216 million
3. Pfizer's Xeljanz: $167 million
4. Eli Lilly's Trulicity: $145 million
5. Pfizer and Bristol-Myers Squibb's Eliquis: $142 million
6. Merck's Keytruda: $127 million
7. Bayer and Johnson & Johnson's Xarelto: $120 million
8. Eli Lilly's Taltz: $116 million
9. GlaxoSmithKline's Breo: $103 million
10. Novartis' Cosentyx: $100 million
11. Novo Nordisk's Victoza: $98 million
12. AstraZeneca's Farxiga: $87.4 million
13. Boehringer Ingelheim and Eli Lilly's Jardiance: $86.9 million
14. Bristol-Myers Squibb: Opdivo: $82 million
15. Celgene's Otezla: $78 million
16. Gilead's Harvoni: $75 million
17. Allergan's Linzess: $73 million
18. Novartis' Entresto: $71 million
19. Otsuka and Lundbeck's Rexulti: $69 million
20. Johnson & Johnson's Invokana: $63 million
Saturday, July 28, 2018
Thursday, July 26, 2018
These are the websites your clean-install Windows PC connects to by itself - MSPoweruser
Dual Nationality
7 Simple Steps to Help You Shoot an Interview
Wednesday, July 25, 2018
2018-07/28 How to Create a Podcast with Adam Greenfield | My Site
Tuesday, July 24, 2018
DEF CON IV Archives
Co-Chair of the Computer Ethics and Responsibilities Campaign.
Monday, July 23, 2018
END OF ANDROID? Fears Google may be SCRAPING hugely popular mobile OS | Express.co.uk
https://www.express.co.uk/life-style/science-technology/992004/Android-update-Google-replacing-smartphone-OS-with-Fuchsia-claims