Just a basic blog—snagging random stuff that catches our eye—nothing else, really...
Tuesday, October 30, 2018
Cimetrics BACnet Explorer
Cimetrics BACnet Explorer: With “plug-and-play”, BACnet Explorer for BACnet/IP you can discover BACnet devices on connected networks. Connect Explorer to a BACnet Network and it will automatically discover and display a listing of all BACnet devices on that network.
Amazon Patched Multiple IoT Vulnerabilities Affecting Its Smart Devices
Amazon Patched Multiple IoT Vulnerabilities Affecting Its Smart Devices: "Recently, Amazon patched multiple IoT vulnerabilities present in its operating system for smart devices. The vulnerabilities could have allowed hackers to take complete control of the device and execute remote commands. These security flaws affected numerous smart home products of Amazon as well as its AWS modules."
Monday, October 29, 2018
Heatmiser and BMW – Better Connected with IFTTT | Heatmiser
Heatmiser and BMW – Better Connected with IFTTT | Heatmiser: "Connecting the Heatmiser & BMW Channels means your BMW can communicate with your Neo & SmartStat." WCPGW
No One Can Get Cybersecurity Disclosure Just Right | WIRED
No One Can Get Cybersecurity Disclosure Just Right | WIRED
Fer?
https://www.wired.com/story/cybersecurity-disclosure-gdpr-facebook-google/Sunday, October 28, 2018
The White House is wooing tech workers to do tours of duty in government - The Washington Post
The White House is wooing tech workers to do tours of duty in government - The Washington Post: The White House plans to convene technology giants including Amazon.com, Google, Microsoft and IBM on Monday and urge them to make it easier for their workers to leave behind their big paychecks and snazzy office perks and do brief tours of duty in government.
132 Women In Cybersecurity To Follow On Twitter
132 Women In Cybersecurity To Follow On Twitter: "The compilation started earlier this week with an inaugural list of 58 women in cybersecurity to follow on Twitter – including CISOs, IT security pros, cybersecurity company founders and CEOs, entrepreneurs, community organizers, investors, government workers, journalists, and more."
‘War for Talent’ Emerges Amid Skilled Workforce Shortage – WWD
‘War for Talent’ Emerges Amid Skilled Workforce Shortage – WWD: "The global survey found that 62 percent of respondents are “struggling to fill skilled roles” across the supply chain and, as a result, “fashion retailers, brands, manufacturers and vendors face a shortage of workers with key, specialized skills.""
Saturday, October 27, 2018
Amazon fixes security flaws allowing smart home hijacks
Amazon fixes security flaws allowing smart home hijacks
https://www.engadget.com/2018/10/21/amazon-fixes-13-iot-security-flaws/
https://www.engadget.com/2018/10/21/amazon-fixes-13-iot-security-flaws/
New state-backed espionage campaign targets military and government
New state-backed espionage campaign targets military and government using freely available hacking tools | ZDNet
https://www.zdnet.com/article/new-state-backed-espionage-campaign-targets-military-and-government-using-freely-available-hacking/
https://www.zdnet.com/article/new-state-backed-espionage-campaign-targets-military-and-government-using-freely-available-hacking/
Friday, October 26, 2018
Cybersecurity Needs Women: Here's Why
Cybersecurity Needs Women: Here's Why
https://www.forbes.com/sites/laurencebradford/2018/10/18/cybersecurity-needs-women-heres-why/
Good quotes...
https://www.forbes.com/sites/laurencebradford/2018/10/18/cybersecurity-needs-women-heres-why/
TRITON Attribution: Russian Government-Owned Lab Most Likely Built Custom Intrusion Tools for TRITON Attackers � TRITON Attribution: Russian Government-Owned Lab Most Likely Built Custom Intrusion Tools for TRITON Attackers | FireEye Inc
TRITON Attribution: Russian Government-Owned Lab Most Likely Built Custom Intrusion Tools for TRITON Attackers: "FireEye Intelligence assesses with high confidence that intrusion activity that led to deployment of TRITON was supported by the Central Scientific Research Institute of Chemistry and Mechanics (CNIIHM; a.k.a. ЦНИИХМ), a Russian government-owned technical research institution located in Moscow."
ICS Cyber Security | Protect Against Threats - Nozomi Networks
ICS Cyber Security | Protect Against Threats - Nozomi Networks: "The Nozomi Networks solution improves ICS cyber resiliency and provides real-time operational visibility. Major customers have improved reliability, cyber security and operational efficiency using our technology."
Thursday, October 25, 2018
The U.S. labor shortage is reaching a critical point
The U.S. labor shortage is reaching a critical point: "The Bureau of Labor Statistics reported that April closed with 6.7 million job openings."
Top Five Sectors Exposed to Labor Shortages in 2018 – Industry Insider
Top Five Sectors Exposed to Labor Shortages in 2018 – Industry Insider: "December 2017, a record 82.0% of builders reported labor shortages as a significant problem,"
Full text of Apple CEO Tim Cook's keynote in Brussels
Full text of Apple CEO Tim Cook's keynote in Brussels: "We are responsible, however, for recognizing that the devices we make and the platforms we build have real, lasting, even permanent effects on the individuals and communities who use them."
The pilot shortage isn't changing course. Here's how UPS plans to land new talent.
The pilot shortage isn't changing course. Here's how UPS plans to land new talent.
https://www.courier-journal.com/story/money/companies/2018/09/17/ups-pilot-shortage-new-training-program/1210341002
https://www.courier-journal.com/story/money/companies/2018/09/17/ups-pilot-shortage-new-training-program/1210341002
Airlines are desperate for pilots and it's causing route cancellations - Business Insider
Airlines are desperate for pilots and it's causing route cancellations - Business Insider
https://www.businessinsider.com/airlines-pilot-shortage-cancelled-routes-2018-8
https://www.businessinsider.com/airlines-pilot-shortage-cancelled-routes-2018-8
Wednesday, October 24, 2018
Security Manager - (Pacific Northwest) - Job ID: 666060 | Amazon.jobs
Security Manager - (Pacific Northwest) - Job ID: 666060 | Amazon.jobs: Managing a large guard force across multiple regions throughout – as well as serving in support roles to the global team
Skills gap stalls construction industry growth, report says | HR Dive
Skills gap stalls construction industry growth, report says
https://www.hrdive.com/news/skills-gap-stalls-construction-industry-growth-report-says/531442/Aerospace Skills Gap: Workforce Declines, As Talent Needs Increase - Area Development
Aerospace Skills Gap: Workforce Declines, As Talent Needs Increase - Area Development
http://www.areadevelopment.com/Aerospace/q3-2015-auto-aero-site-guide/Aerospace-Skills-Gap-Workforce-Declines-Needs-Increase-45711.shtml
http://www.areadevelopment.com/Aerospace/q3-2015-auto-aero-site-guide/Aerospace-Skills-Gap-Workforce-Declines-Needs-Increase-45711.shtml
One Company’s Solution To The Widening Skills Gap
One Company's Solution To The Widening Skills Gap
https://chiefexecutive.net/one-companys-solution-widening-skills-gap/
https://chiefexecutive.net/one-companys-solution-widening-skills-gap/
Monday, October 22, 2018
Study Finds Diversity Boosts Innovation in U.S. Companies | NC State News | NC State University
Study Finds Diversity Boosts Innovation in U.S. Companies | NC State News | NC State University
https://news.ncsu.edu/2018/01/diversity-boosts-innovation-2018/
https://news.ncsu.edu/2018/01/diversity-boosts-innovation-2018/
Sunday, October 21, 2018
Is It “Techno-Chauvinist” & “Anti-Humanist” to Believe in the Transformative Potential of Technology?
Is It “Techno-Chauvinist” & “Anti-Humanist” to Believe in the Transformative Potential of Technology?: "technological advancement solves far more problems than it creates by helping to reduce hunger and disease, travel further, communicate more widely, gain leisure time, and so on." Adam Thierer
Friday, October 19, 2018
Thursday, October 18, 2018
GDPR matchup: The California Consumer Privacy Act 2018
GDPR matchup: The California Consumer Privacy Act 2018: In this installment, Lydia De La Torre, CIPP/US, compares the new California Consumer Privacy Act 2018 to the GDPR.
Data breach response plans are no longer optional for public practices. Here’s what yours needs. | INTHEBLACK
Data breach response plans are no longer optional for public practices. Here’s what yours needs. | INTHEBLACK: "Now that many small businesses are required to report and respond to a data breach – and do so within 30 days – it pays to have a response plan in place to protect client confidence and avoid reputational damage." Security down under...
Tuesday, October 16, 2018
New Climate Debate: How to Adapt to the End of the World - Bloomberg
New Climate Debate: How to Adapt to the End of the World - Bloomberg
M3
https://www.bloomberg.com/news/articles/2018-09-26/new-climate-debate-how-to-adapt-to-the-end-of-the-worldJeff Bezos: Tech will figure out the solutions to abuse
Jeff Bezos: Tech will figure out the solutions to abuse
M3
https://www.cnbc.com/2018/10/15/jeff-bezos-tech-will-figure-out-the-solutions-to-abuse.htmlStephen Hawking warned of 'superhumans' and the end of humanity
Stephen Hawking warned of 'superhumans' and the end of humanity
M3
https://www.sciencealert.com/stephen-hawking-future-superhumans-threaten-end-humanity-genetic-engineering-crispr-evolution-ai-planet?perpetual=yes&limitstart=1Sunday, October 14, 2018
One-Third of US Adults Hit with Identity Theft
One-Third of US Adults Hit with Identity Theft: "One-third of adults in the United States have experienced identity theft, putting them far ahead of other nations. Thirty-three percent is double the global average and more than three times the rate of people in France and Germany."
Saturday, October 13, 2018
What is the difference between categorical, ordinal and interval variables?
What is the difference between categorical, ordinal and interval variables?: "In talking about variables, sometimes you hear variables being described as categorical (or sometimes nominal), or ordinal, or interval. Below we will define these terms and explain why they are important."
Everything You Need to Know about NERC CIP Compliance by Dave Millier, CRISC - security management, risk, risk management & compliance
Everything You Need to Know about NERC CIP Compliance by Dave Millier, CRISC - security management, risk, risk management & compliance: Within the industry of cybersecurity,there is a non-profit organization that ensures the reliability and security of bulk power transmission in north america (USA, Canada, and Mexico).
Welcome to Triumph Music | Production Music Library
Welcome to Triumph Music | Production Music Library: "Welcome to Triumph Music’s brand new website. We have been working with the best composers, graphic designers, web developers and Made Up Music to bring the audio visual community a production library like no other."
Features - Statistical Test Selector | Laerd Statistics
Features - Statistical Test Selector | Laerd Statistics: "It is common for students and researchers to collect good data, but report the wrong findings because they selected the incorrect statistical tests to analyse their data with."
Cloud Baby Monitor - Unlimited Range Video Baby Monitor
for iPhone, iPad, iPod touch, Mac, Apple TV, and Apple Watch
https://cloudbabymonitor.com/LIRR to Jamaica and Airtrain: Best Way to Get to JFK
LIRR to Jamaica and Airtrain: Best Way to Get to JFK...
https://travelsort.com/lirr-to-jamaica-and-airtrain-best-way-to-get-to-jfk/Thursday, October 11, 2018
Pearson Correlation - SPSS Tutorials - LibGuides at Kent State University
Pearson Correlation - SPSS Tutorials - LibGuides at Kent State University:
'The magnitude, or strength, of the association is approximately moderate (.3 < | r | < .5)."
Weight and height have a statistically significant linear relationship (p < .001).
The direction of the relationship is positive (i.e., height and weight are positively correlated), meaning that these variables tend to increase together (i.e., greater height is associated with greater weight).
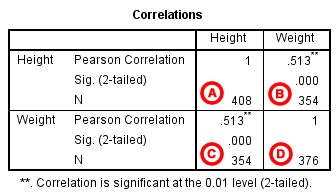
'The magnitude, or strength, of the association is approximately moderate (.3 < | r | < .5)."
Weight and height have a statistically significant linear relationship (p < .001).
The direction of the relationship is positive (i.e., height and weight are positively correlated), meaning that these variables tend to increase together (i.e., greater height is associated with greater weight).

What is the difference between categorical, ordinal and interval variables?
What is the difference between categorical, ordinal and interval variables?: "A categorical variable (sometimes called a nominal variable) is one that has two or more categories, but there is no intrinsic ordering to the categories. For example, gender is a categorical variable having two categories (male and female) and there is no intrinsic ordering to the categories. Hair color is also a categorical variable having a number of categories (blonde, brown, brunette, red, etc.) and again, there is no agreed way to order these from highest to lowest. A purely categorical variable is one that simply allows you to assign categories but you cannot clearly order the variables. If the variable has a clear ordering, then that variable would be an ordinal variable, as described below."
Gender bias in health care may be harming women's health
Gender bias in health care may be harming women's health: From the way medicines are researched and tested, to the approach doctors take diagnosing and treating diseases, more and more research shows a bias against women in the health care system.
Wednesday, October 10, 2018
Email and Internet Voting: The Overlooked Threat to Election Security - Common Cause
Email and Internet Voting: The Overlooked Threat to Election Security - Common Cause: As state election officials grapple with the looming threat of cyberattack on election technology, there is a significant vulnerability that has been roundly ignored: transmission of ballots over the internet, including by email, fax and blockchain systems.
U.S. GAO - Weapon Systems Cybersecurity: DOD Just Beginning to Grapple with Scale of Vulnerabilities
U.S. GAO - Weapon Systems Cybersecurity: DOD Just Beginning to Grapple with Scale of Vulnerabilities: In recent cybersecurity tests of major weapon systems DOD is developing, testers playing the role of adversary were able to take control of systems relatively easily and operate largely undetected.
Monday, October 8, 2018
Tuesday, October 2, 2018
Facebook pulls its Onavo Protect VPN app from Apple's App Store
Facebook pulls its Onavo Protect VPN app from Apple's App Store: "However, it reportedly violated Apple’s guidelines for apps, which don’t allow them to gather user data into databases and sell it to third parties. It also came under fire for running analytics on the traffic that it routed through its servers as part of its VPN service – which amounted to another way to collect information on users’ activity."
Subscribe to:
Comments (Atom)